This is a write-up about how I solved the sixth episode of the H4CK1NG GOOGL3 security CTF. If you didn't read my post about the first episode, I highly recommend you to check it out since it introduces the concept of a CTF.
It took me quite a while to write those write-ups (especially this one - the last one), so I kept it rather short this time. The more exciting challenges were the first couple ones, anyways.
Challenge 01: Small Toys
Hints:
- One of the researchers really liked small toys.
The first challenge came with a binary file containing data that I could not really make sense of:
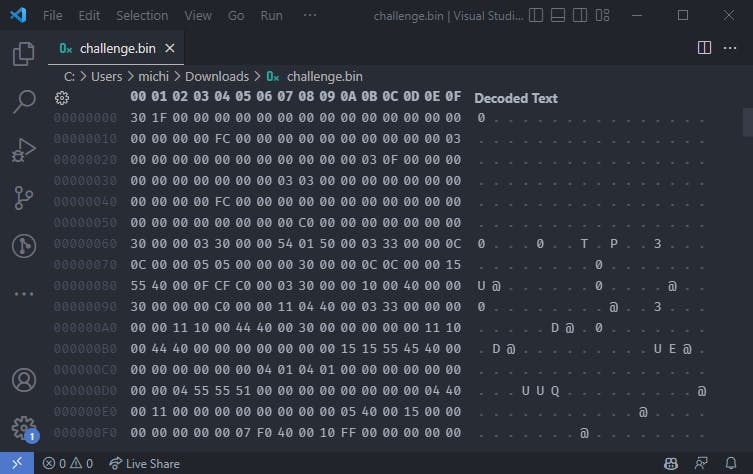
Someone hinted to me that in the video that is provided with each challenge, one of the researchers really liked small digital toys. So it became clear that this has to be some kind of graphical data for some old black and white display. Maybe there were talking about Tamagotchis?
It took me quite a while to figure out the image format. Turns out it's an animation sheet with multiple smaller pictures that use some weird padding. Also, it actually contains greyscale color information, so not only black & white.
So I wrote a Python script to parse this weird format and convert it into jpg files. One of the resulting images looked like this:
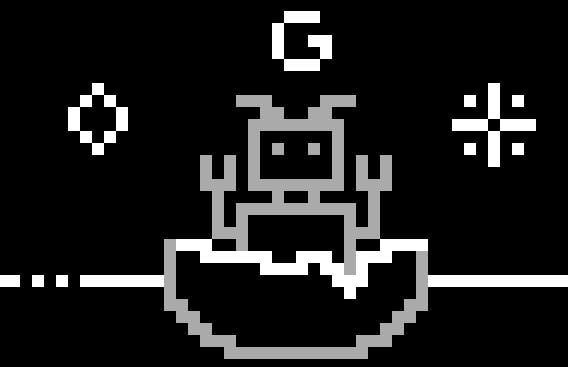
Putting all images in a line reveals some text containing the flag.
Challenge 02: Bleichenbacher
Hints:
- Have you heard of Bleichenbacher?
This was definitely the hardest (and most annoying) challenge, and that took me the most time.
The challenge presented you with a game (including it's source code) where you try to hit buttons at the right time to kill the bugs in your way - at least that's what I think it is about, never really played it for longer than a couple of seconds.

From the source code, it became apparent that the flag will be revealed once the player achieves an integer overflow (for example, by successfully submitting a score of -1). The source code of the game itself wasn't too interesting, other than the fact that they implemented their own cryptography library to work with signatures, which sign the high score and send it to the scoreboard API (which is written in Python).
The crypto library had some issues that would allow for forging the signature using the so-called Bleichenbacher 06 attack. This is quite complicated, and I don't want to go too deep into this topic. However, it was not the standard vulnerability and worked a bit differently. Basically, one had to pass multiple checks by exploiting the padding and putting garbage into some parts of the signature.
Challenge 03: Morse Code
Hints:
- There is morse code hidden somewhere
The third challenge was a bit different than the previous ones since it required you to go back to all the videos that came with each challenge and piece together a secret message.
Each video contained some morse code, which was audible but really hard to write down. So I did a spectral analysis of each part where I heard some beeping, and there the long and short beeps were more obvious:

However, the message that came out contained a flag that did not work. They later announced at the event Discord that there was a mistake and provided the correct part.
Conclusion
The first challenge was quite fun, though I did not enjoy the others as much. However, all in all, a really fun (but quite a time intensive) CTF!
Episode Overview:

